Cedolare_secca._Vademecum_adempimenti
Agevolazioni_assunzioni._Sgravi_a_confronto
Benefici_prima_casa._Come_cambiano_dal_2016
Locazioni_turistiche._La_disciplina_fiscale
Prestazioni_gratuite_del_professionista
I also recommend to read all the related topics about GSM that are explained in the rtl-sdr.com blog, and the next are all the links recommended before beginning with this task:
1) First I recommend you to memorize the GSM non-hopping downlink channel appearance and noise to recognize it when using gqrx or other softwares: http://www.rtl-sdr.com/signal-identification-guide/
2) After getting used to this signal, a good point to begin is: http://www.rtl-sdr.com/rtl-sdr-tutorial-analyzing-gsm-with-airprobe-and-wireshark/
To setup all the necessary software you will need to perform this task, so I had followed this link. I have to alert you that some linux distributions may not be able to get airprobe working. In my case I tried first to get airprobe at ubuntu 12.04 LTS operating system and I can’t get it working, so the solution is to install at your PC the Kali Linux operating system that is a perfect system to use airprobe. It comes with some radio features that enhance the experience of anyone who likes sniffing diferent types of signals.
Although the link installs the gnuradio and gqrx softwares via an install script, I recommend you to go to the Ubuntu Software Center or in case you use Kali linux, I recommend to use the program to install/update/remove software named: Add/Remove Software, which is placed at Applications > System Tools > Add/Remove Software.
Once you have this software opened, look for gnuradio packets and install all of them. If it doesn’t find gnuradio, you have to install Ubuntu Software Center at Kali linux operating system and it will find the gnuradio packets for sure. This is the best way of installing gnuradio because the system will compile all the necessary scripts without any problem and all the related packets will be installed too.
At the next link, there are some explanations of how to update softwares available in Kali linux: http://www.linuxbsdos.com/2013/03/23/how-to-install-software-on-kali-linux/
After installing gnuradio and check that it works well, the next step is to install the gqrx software by the same way I have described you to install gnuradio.
After getting gqrx running correctly, you will have to compile airprobe software using the steps at the link above, and if all goes well you will have to get it working correctly without any problem.
3) Before beginning with all the GSM documentation, to understand how the system works, I also recommend you to install the Kalibrate tool to identify where are the principal GSM channels in your area. You can setup this software using this other link: http://www.rtl-sdr.com/how-to-calibrate-rtl-sdr-using-kalibrate-rtl-on-linux/
This software is used to calibrate the RTL-SDR USB dongle offset and know if you are tunning on the exact frequency or you are working with some offset. But in our case, we will use this tool to identify the most powerful GSM channels in our area.
4) Other two posts are interesting for you to read before the beginning:
http://www.rtl-sdr.com/receiving-decoding-decrypting-gsm-rtl-sdr-youtube-talk-slides/ (The video of this link will make you some idea of how is the procedure to crack a GSM call)
http://www.rtl-sdr.com/receiving-decoding-decrypting-gsm-signals-rtl-sdr/ (This other link will bring you to the blog that I talk about some lines above, which is the main blog I worked with to get used to this complex objective)
5) Finally, it was posted few weeks ago another topic about a new tool called pytacle that improves the situation using the Kraken tool to get all the procedure runnning with only using this software:
http://www.rtl-sdr.com/pytacle-gsm-decodingdecrypting-tool-now-supports-rtl-sdr/
But I want to remark that I have not used this software because it runs with the kraken tool, and I personally can’t get the Kraken tool running no way.
Anyway it’s intetersting to see this tool working in the video shown in the link.
The problem is that the kraken tool needs a separate GPU core to realize hard CPU spending tasks with the A5/1 tables to unencypt the frames of GSM. The separate GPU that Karsten Nohl recommended to me by mail is an ATI 5xxx GPU.
Here is the link to download the A5/1 rainbow tables that use the kraken tool: https://opensource.srlabs.de/projects/a51-decrypt/files (You can download them from torrent with any linux distribution and I recommend you to download the last file which is a .tgz and contains all of the above tables)
So I recommend not to take this way and continue reading.
Documentation LINKS:
1) Read the first post of the blog of Domi to see in a big way how the GSM system works:
http://domonkos.tomcsanyi.net/?p=418
2) Then all the things that you don’t understand can be found here: https://skydrive.live.com/view.aspx?resid=8F7DEEEC761F130B!603&app=WordPdf&wdo=2&authkey=!AN3UlLqs7FxmZmQ (in my case, this document has helped me in understanding the complex GSM system so many times that I can’t count them.)
3) Other interesting documents that can help you understanding the GSM system are:
http://deeea.urv.cat/public/PROPOSTES/pub/pdf/1162pub.pdf (This first document is a Master Thesis of a student from the Rovira i Virgili University from Tarragona(Catalonia) that treats the topic “Deployment of a Mobile telephony GSM/GPRS system in the area of Tarragona”, a city about 100 Km from Barcelona; the document is in spanish but before the developement fo the project, it really explains very well all the parts of the GSM system.)
http://yo3iiu.ro/blog/wp-content/uploads/2012/04/Evaluating_GSM_hopping1.pdf (There is another document which really shows the steps of the procedure we will realize but it’s pretty outdated, it’s only to make an idea of how will be our procedure.)
http://www.data.ks.uni-freiburg.de/download/misc/practical_exercise_a51.pdf (This is an example of how to crack GSM, like performing an exercise, it’s similar to the last link and it’s pretty outdated too. But to make some ideas is good to read it.)
http://camp.hsbp.org/2013/zer0/gsm.pdf (Finally, here are some slides of Domi, the author of the blog.)
Recommendation: All of the above documents are available to download freely for everyone but in case some links become broken, I recommend anyone who is interested in to contact me and I send the documents which I have previously downloaded.)
Steps to crack your own android phone calls and SMS messages using a Samsung device:
First of all, I want to remark that I’m using a Samsung Galaxy S GT-I9000 device for this task.
In samsung devices with a Stock ROM, when you connect via USB the device to your computer, it will be recognized as a Modem as well as an ADB interface (in case you have the ADB downloaded and installed in your computer) and as a folder with files like images, songs and videos too.
So I don’t know exactly what is the implementation of the Stock ROM software that makes the device to be used like a Modem and communicate with the SIM card through Hyperterminal (in Windows) or Minicom (in Linux) but is a key feature to crack GSM because it’s the only way I have found to get the KC key and the TMSI number.
So if you have a different device like a Sony Ericsson or HTC or others I’m pretty sure that you will not be able to crack your phone calls. In the case you have a Samsung device, you are lucky today!!! So you can be able to get this running until the step I have reached in case you follow my blog.
I also recommend you to flash a Stock ROM in your Samsung device in case you have a Cyanogenmod ROM or any other Custom ROM, If you don’t really know what I’m talking about be quite and don’t get nervous, I will explain all the characteristics about the Android system necessary to get a the correct ROM running on your Samsung device in another thread of this page of my blog.
I will also be really happy if someone could tell me why the Stock ROMs of Samsung make possible the characteristic of being treated as a Modem, so if someone is an expert of the android system I would really be very happy if you contact with me (my mail is in the about page of this blog).
So after this quite a long chatter, we can begin with the principal steps:
STEP 0: Put your Mobile device working only in GSM not in 3G.
Go to the dialer of the phone and enter the following code like if you will want to call someone: *#*#4636#*#*
A new menu will appear and enter Telephone information. Scroll down and go to the option that indicates: Define the prefered network –> and choose GSM only. Make sure that your option is selected and go back.
With this action you have forced the phone to use the GSM network only.
In some phones this option can be chosen in Settings menu –> Inalambric connections –> Mobile network. But in my case it only allows to choose WCDMA (3G) only or WCDMA/GSM prefered. So you have to enter to advanced options to change it.
STEP 1: Capture the data on the main ARFCN.
The main ARFCN for the cell would be the one with the maximum signal strength and this can be determined with kalibrate tool. We use this tool to get the maximum signal strength in a certain moment.
Example of use:
root@kali:/home/SDR/kalibrate-rtl# kal -s GSM900
____________________________________________________________
Found 1 device(s):
0: ezcap USB 2.0 DVB-T/DAB/FM dongle
Using device 0: ezcap USB 2.0 DVB-T/DAB/FM dongle
Found Rafael Micro R820T tuner
Exact sample rate is: 270833.002142 Hz
kal: Scanning for GSM-900 base stations.
GSM-900:
chan: 74 (949.8MHz – 39.881kHz) power: 100204.30
chan: 101 (955.2MHz – 39.456kHz) power: 91973.50
chan: 108 (956.6MHz – 39.531kHz) power: 181214.37
chan: 115 (958.0MHz – 39.590kHz) power: 65380.82
____________________________________________________________
STEP 2: Identify your service provider’s frequencies and the BTS towers identification numbers.
In my case, VODAFONE Espanya is my service provider and I identified that the frequency range assigned to them in Spain is between: 949,9 – 959,9 MHz. I found this information in wikipedia: http://wiki.bandaancha.st/Frecuencias_telefon%C3%ADa_m%C3%B3vil
Do a google search for your country and for sure you will get success. It’s important to notice that the GSM900 downlink band is between: 935 – 960 MHz.
Another thing that you must take into account is that airprobe is only able to decode the GSM downlink frequency channel.
So after identifing your own service provider frequency range, you have to look for those frequencies in Kalibrate tool that are inside the range of your service provider. These are the frequencies you have to tune with the RTL-SDR USB dongle to find your call or SMS.
The other thing you must know is what MNC and MCC numbers are the ones that identify your service provider’s BTS towers and your country number, respectively. I recommend you to look for them at this link: http://es.wikipedia.org/wiki/MCC/MNC (in Spanish, but you can translate it with your browser)
Here is explained what are the MNC and MCC numbers and which are the ones for your country (MCC) and for your service provider (MNC).
These numbers can be used to place in a map the BTS towers you are using at a specified moment. The following web page will shoe you how a map and the situation of BTS towers with the input of your MNC and MCC numbers: http://www.opencellids.org/en/opencellid/cell-location
STEP 3: Get your mobile’s TMSI number.
This number is the one that is assigned to your phone when it is paged and is going to comunicate with the BTS tower. So this is the number that the BTS will use to identify your mobile device. To get this number I used the AT commands procedure to get acces to the SIM card of the mobile device where this number is stored and then I followed this link to enter the specific AT commands for this case: http://openbsc.osmocom.org/trac/wiki/A5_GSM_AT_tricks (it also shows how to obtain the Kc key, this key will be necessary for decrypting the GSM information and get the data of our call or SMS).
The following link explains some more options to get the Kc key that we will have to obtain later for decrypting: http://domonkos.tomcsanyi.net/?p=369 (I used the procedure of the link above to get the Kc key and the TMSI number, so I don’t know if the other options will work or not).
To identify the TMSI number in wireshark, just read this document to know what type of GSM frames can you find in wireshark:
________________________________________________________________________
GSM Message types: All these messages are from the MS(Mobile Station) to the BTS!!! (the so named air frame)!!! They are only signalling messages.
This first type of messages contains information of the BTS towers (of the system).
A) System Information Types:
Type 1: Channel type = BCCH (But GSM CCCH Info)
LIST of ARFCNs of the cell!!!
RACH control parameters.
Type 2: Channel type = BCCH (But GSM CCCH Info)
Neighbour cell description like LIST of ARFCN’s of the cell.
Neighbour cell description – BCCH frequency list.
Type 3: Channel type = BCCH (But GSM CCCH Info)
Cell identity code decoded, LAI(MCC+MNC+LAC)decoded and some GPRS information.
Type 4: Channel type = BCCH (But GSM CCCH Info)
LAI(MCC+MNC+LAC) decoded, Cell selection parameters and RACH control parameters. Some GPRS information too.
Type 2ter: Channel type = BCCH (But GSM CCCH Info)
Neighbour cell description like LIST of ARFCN’s of the cell.
Neighbour cell description – Extended BCCH frequency list.
Typer 2quater: Channel type = BCCH (But GSM CCCH Info)
3G message with information that we don’t take into account in this study. Like 3G neighbour cell description.
Type 13: Channel type = BCCH (But GSM CCCH Info)
They contain all the important information about GPRS like GPRS Cell options, GPRS Power Control Parameters.
This second type contains information of the Mobile Station (MS).
B) Paging Request Types:
Type 1: Channel type = CCCH (And GSM CCCH Info)
Mobile Identity 1 number (IMSI)
Page Mode = normal paging (P1)
Channel Needed
Mobile Identity 1 and 2 = TMSI/P-TMSI
Page Mode = normal paging (0)
Channel Needed
I altres tipus de Paging Request Type 1 poden portar qualsevol combinació d’identificadors de la MS com per exemple TMSI/P-TMSI del MS1 i IMSI del MS2 o IMSI del MS1 i MS2, etc.
Només el IMSI del MS1 o bé No idnetity code, etc.
Type 2: Channel type = CCCH (And GSM CCCH Info)
Mobile Identity 1 and 2 = TMSI/P-TMSI i IMSI del Mobile Idnetity 3
Page Mode = normal paging (0)
Channel Needed
Type 3: Channel type = CCCH (And GSM CCCH Info)
Mobile Identity 1, 2 , 3 and 4 = TMSI/P-TMSI (Not decoded)
Page Mode = normal paging (0)
Channel Needed
C) Immediate Assignment: Channel type = CCCH (And GSM CCCH Info)
Time Advance Value
Packet Channel Description (Time Slot)
Page Mode = Extended Paging(1)
________________________________________________________________________
STEP 4: Use the rtl_sdr tool to sniff all the information of the channel you have found.
The rtl_sdr tool comes with gnuradio and it will catch all the information with the RTL dongle and save it in a .bin file at the directory that you want to save it.
Example of use:
./rtl_sdr /tmp/rtl_sdr_capture.bin -s 1.0e6 -f 957e6 -g 44.5
So in this case, the tool will save the data into a file named: rtl_sdr_capture.bin and placed inside the tmp directory. The -s flag is to specify the sample rate which seems to be better than the 1.8e6 which is the default one. The other settings are the frequency which we want to tune and the gain.
I prefer to decode a live channel that use top_block tool that comes with airprobe to get the information because this tool seems to be not as efficient as the rtl_sdr that have a bandwidth of 3.5MHz which is enough to include all the GSM channel with the frequencies the system can change during the call.
As we know the GSM is a frequency hopping system that will change the transmitter and receiver frequency in a call following the pattern of ARFCNs received in the System Information Type 1 frames before setting the call.
STEP 5: Convert the .bin file into a .cfile file with a precompiled gnuradio-companion scheme.
The gnuradio-companion is a tool that comes with gnuradio and it has a graphical interface. You must download the next file: http://sdr.osmocom.org/trac/attachment/wiki/rtl-sdr/rtl2832-cfile.grc (Go to the end of the page and click on download in original format).
After this, open gnuradio-companion by typing it in a terminal prompt:
gnuradio-companion
And the program will open, the go to the tab open file and search the downloaded file named: rtl2832-cfile.grc.
Set the file source to the capture.bin file directory where you have saved it with in the previous STEP 3, and set the file output for a file called capture.cfile which should be located in the ‘airprobe/gsm-receiver/src/python’ folder. Also, make sure that ‘Repeat’ in the File Source block is set to ‘No’.
Now execute the GRC flow graph by clicking on the icon that looks like grey cogs. This will create the capture.cfile. The flow chart will not stop by itself when it’s done, so once the file has been written press the red X icon in GRC to stop the flow chart running. Because it won’t stop by itself.
Then you can close the gnuradio-companion and delete the .bin file saved in the tmp directory.
STEP 6: Open and setup wireshark:
Open another terminal prompt and to open wireshark with sudo privileges:
wireshark
Note that it’s always better to work with sudo privileges when using airprobe, wireshark, gnruadio, etc.
Then the wireshark software will open and you must select lo(loopback) and start. Note that wireshark comes installed in kali linux.
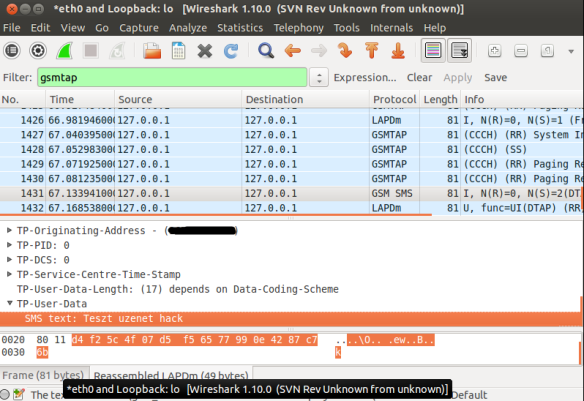
When a window which is capturing is opened go to the filter box and write gsmtap to see only the GSM frames.
STEP 7: Finally use the go.sh tool that comes with airprobe to send the decoded information to wireshark and analyze the frames.
First, we have to decode the signalling frames to know more things about the calls we are decoding:
./go.sh capture.cfile 64 0B
The 64 is the decimation rate of the RTL-SDR, 0B is the configuration which go.sh is going to use: 0 means Timeslot 0 (beacon channel), B is the configuration that the cell uses on the beacon channel.
With this we will get information about the system and of the calls identification numbers TMSI or IMSI(in few cases).
The information that contains any frame of signalling will be explained in a new thread in the next days.
STEP 8: Procedure and configuration of airprobe to identify all the information and decode it.
As this part is perfectly explained in the Domi’s blog, this is the same explanation:
a) Decoding an SMS:
Here are all the available configurations that are supported by airprobe:
0C : TimeSlot0 "Combined configuration", with SDCCH/4
(FCCH + SCH + BCCH + CCCH + SDCCH/4)
0B : TS0 "FCCH + SCH + BCCH + CCCH"
1S : TS1 SDCCH/8
2T : TS2 (Full Rate) Traffic
1TE: TS1 Enhanced Full Rate Traffic
As you can see these are the GSM configurations used in the different frames and you will have to be able to recognize each one to identify if you must use an airprobe configuration or another to decode the data of your call or SMS.
If you look at the traffic in Wireshark but it doesn’t seem to be right (for example you made a call or sent a text message while capturing but the Ciphering Mode Command is missing) it is pretty sure that you are using the wrong configuration (0B instead of 0C or vise versa). It is important to try both and figure out which one is correct for the cell you are observing.
I will assume you sent a text message to yourself while capturing data.
So now you can see all the messages of the beacon channel, but what are you looking for in the Wireshark log? It is quite simple: first a “Paging Request” for the TMSI of the target phone, then a “Ciphering Mode Command”. These are the messages which indicate that a transaction actually happened.
Now to continue with the flow it is best to try to decode the same cfile but now giving the key too to go.sh:
./go.sh capture.cfile 64 0C KEY
I will explain how to get the Kc key with my method in a later thread.
What are we looking for now? Well, it depends on the network: either there is an “Immediate Assignment” telling the phone to move to different timeslot (so they are not using the busy beacon channel to do their business) or you will actually be able to see the text message.
If instead of the SMS you find an “Immediate Assignment” message you need to open it and see which timeslot the phone is being commanded to and then you need to decode that timeslot using go.sh. So, for example if it says that the phone needs to go to Timeslot 2 then your command would be:
./go.sh capture.cfile 64 2S KEY
Notice that I did not only change the Timeslot number from 0 to 2, but also the configuration from C to S, because the target phone is now on a Standalone Dedicated Control Channel (SDCCH), not on the beacon channel so we need to decode it differently.
Also worth noting that SMS messages are almost always sent on the Control Channel not on the Traffic Channel.
Here is a flowchart of the whole process to make it easier to understand (naturally since we can only see the downlink this shows only what happens on the downlink):
b) Decoding a Voice call:
Now that we were able to decode an SMS let’s get to something a little bit harder: decoding a voice call!
Well the first step is the same as it was when we decoded a text message: we look at the beacon channel, Timeslot 0:
./go.sh capture.cfile 64 0C
What do we expect to see? Nothing besides the “Cipher Mode Command” because we didn’t provide the key, so let’s do that:
./go.sh capture.cfile 64 0C KEY
All right, what should we see now? Logically there needs to be an “Immediate Assignment” command, because the phone NEEDS to change at least once to a different timeslot to receive voice data (to a Traffic Channel, Timeslot 1-7). What we saw when decoding the SMS is correct here too: depending on the network configuration we can see some messages about the call setup (if it is an incoming call we can even see the caller ID – the phone number calling our target) then an “Immediate Assignment” (configuration ‘C’ – combined) or we can only see an “Immediate Assignment” directing the phone to a Control Channel (just like it happened when receiving an SMS, configuration ‘B’).
Of course if you follow the phone to the Control Channel you will see the call setup messages (in case of an incoming call) then another “Immediate Assignment” command, this time directing the phone to a Traffic Channel.
Here is again a flow chart showing the process:
Now there is only one question left: how do we decode the traffic channel to actually get the voice data?
Again, it is something that depends on the network: if the network uses simply Full Rate Speech then you can do the same what has been written in Srlabs’s tutorial:
./go.sh capture.cfile 64 1T KEY
What does this command do? It decodes Timeslot 1 as a Traffic Channel. We know what timeslot to decode from the “Immediate Assignment” command message, T means Full Rate Speech. The command results in a file called “speech.au.gsm”, which needs to be converted to .au file using ‘toast’:
toast -d speech.au.gsm
The toast tool is a software to convert files and I will explain the setup process of this software on another thread.
The resulting .au file could be played back using any player, e.g. cvlc (Command Line VLC):
cvlc speech.au
So you must download and install VLC player too.
If you can not hear anything but beeps and other weird noises then there is a pretty good chance that the cell is using Enhanced Full Rate Speech instead of simple Full Rate Speech.
To decode the channel as an Enhanced Full Rate Speech Traffic Channel:
./go.sh capture.cfile 64 1TE KEY
This results in a file called “speech.amr” which could be played back without any more modifications using for example Commandline VLC:
cvlc speech.amr
All the threads related to this topic will be classified under the category of GSM software setup!!! You can read them on the first page!!!
Per chi capisce le frequenze di downlink sono:
1844000000 TIM H3G
1854600000 WIND
RICORDA
L’IMSI, International Mobile Subscriber Identity, è il codice che identifica una coppia SIM-operatore telefonico, ossia la SIM all’interno di una rete GSM di un certo operatore. Il codice IMSI è lungo 15 cifre ed è così composto:
grgsm_capture.py -p 11 -g 30 -c cattura.cfile –band=DCS1800 -f 1854.6e6
Il comando da digitare su shell è:
sudo mount -t cifs “//192.168.30.205/caf” -o guest,noperm,rw “/mnt/caf”
Il comando di cui sopra è per l’utente guest con permessi di lettura e scrittura.
Per montare una cartella windows acronis sul pc 192.168.30.110 e con la specificazione della user e password
sudo mount -t cifs -o username=utente,password=password //192.168.30.110/acronis /mnt/directory
In linux sulla shell:
git clone https://github.com/steve-m/kalibrate-rtl
cd kalibrate-rtl
sudo kal -s GSM900
Otterrete l’elenco dei canali. Prendete il canale con la frequenza piu’ alta. Poi il comando con l’opzione -c canale nel mio caso il canale 34
sudo kal -c 34
Otterrete average absolute error: 12.642 ppm
Metterete al bisogno il valore ppm o 12 o 13
per fare lo scanning delle frequenze grgsm_scanner -p 13
Per calcolare un hash md5 puoi usare il seguente comando con l’uso della pipe
md5sum nome_file.ext | awk ‘{ print $2, $1 }’
Scarica file:
#!/bin/bash
URL=”https://api.hubic.com”
CLIENTID=”api_hubic_”
CLIENTSECRET=””
USEREMAIL=”com”
USERPWD=””
CREDENTIALS=$( printf “$CLIENTID:$CLIENTSECRET” | base64 -w 0 )
urlen() {
# Thanks https://gist.github.com/cdown/1163649
local length=”${#1}”
for (( i = 0; i < length; i++ )); do
local c=”${1:i:1}”
case $c in
[a-zA-Z0-9.~_-]) printf “$c” ;;
*) printf ‘%s’ “$c” | xxd -p -c1 |
while read c; do printf ‘%%%s’ “$c”; done ;;
esac
done
}
function setup () {
# Obtain request code
OAUTH=$( curl -s –get “https://api.hubic.com/oauth/auth/” –data-urlencode “client_id=$CLIENTID” –data-urlencode “redirect_uri=$URL” –data-urlencode “scope=usage.r,account.r,getAllLinks.r,credentials.r,sponsorCode.r,activate.w,sponsored.r,links.drw” –data-urlencode “response_type=code” –data-urlencode “state=RandomString_mpOwM8gSJD” | grep “name=\”oauth\”” | cut -d” ” -f4 | cut -c8-13 )
if [ $? -ne 0 ]; then
echo “Error getting request code, verify credentials”
exit 1
fi
# Accepting the app itself for the request token
REQUESTTOKEN=$( curl -s -i “https://api.hubic.com/oauth/auth/” –data-urlencode “oauth=$OAUTH” –data-urlencode “action=accepted” –data-urlencode “account=r” –data-urlencode “credentials=r” –data-urlencode “getAllLinks=r” –data-urlencode “links=r” –data-urlencode “links=w” –data-urlencode “usage=r” –data-urlencode “login=$USEREMAIL” –data-urlencode “user_pwd=$USERPWD” –data-urlencode “submit=Accept” | grep Location | cut -c11- | grep code | cut -d”=” -f2 | cut -d”&” -f1 )
if [ $? -ne 0 ]; then
echo “Error getting Request Token, try again later”
exit 1
fi
# Obtaining the auth code
AUTHCODE=$( curl -s “https://api.hubic.com/oauth/token/” -H “Authorization: Basic $CREDENTIALS” –data-urlencode “code=$REQUESTTOKEN” –data-urlencode “redirect_uri=$URL” –data-urlencode “grant_type=authorization_code” | cut -d”\”” -f10 )
if [ $? -ne 0 ] || [ -z “$AUTHCODE” ]; then
echo “Error $? getting Auth Code, try again later.”
exit 1
fi
#Obtaining endpoint and token
curl -s -H “Authorization: Bearer $AUTHCODE” https://api.hubic.com/1.0/account/credentials > /tmp/paso1.txt
if [ $? -ne 0 ] || [ $( cat /tmp/paso1.txt | grep invalid ) ] ; then
echo “Error $? getting token, check your AuthCode”
echo “Debug: ”
cat /tmp/paso1.txt
echo “***********************************”
rm /tmp/paso1.txt
exit 1
fi
TOKEN=$( cat /tmp/paso1.txt | cut -d”\”” -f4 )
ENDPOINT=$( cat /tmp/paso1.txt | cut -d”\”” -f8 )
#Deleting temp file
rm /tmp/paso1.txt
}
if [ $# == 0 ]; then
echo “hubiC cli manager – NetoMX v0.1”
echo “Usage: $0 [-l / -d / -u] [FILE]”
exit 1
fi
if [ “$1” == “-d” ] || [ “$1” == “-u” ] && [ $# != 2 ]; then
echo “hubiC cli manager – NetoMX v0.1”
echo “Usage: $0 [-l / -d / -u] [FILE]”
exit 1
fi
case “$1” in
“-d”) echo “Scarico i files da questo elenco: $2”
setup
elencuccio=./$2
while read line || [[ -n “$line” ]]; do
FILENAME=$( urlen “$line” )
echo “downloading del seguente file:” $line
curl -s -g -H “X-Auth-Token: $TOKEN” “$ENDPOINT/default/documenti/$FILENAME” -X GET -o “$line”
if [ $? -ne 0 ]; then
echo “Error $? downloading file: $1”
exit 1
fi
done < “$elencuccio”
exit 0
;;
“-u”) echo “Uploading file: $2”
setup
curl -s -g -H “X-Auth-Token: $TOKEN” “$ENDPOINT/default/” -X PUT -T “$2”
if [ $? -ne 0 ]; then
echo “Error $? subiendo archivo $2”
exit 1
fi
exit 0
;;
“-l”) echo “Listing files:”
setup
#Uncomment this if you want pretty JSON
#curl -s -H “X-Auth-Token: $TOKEN” $ENDPOINT/default?format=json -X GET | python -m json.tool
curl -s -H “X-Auth-Token: $TOKEN” $ENDPOINT/default?format=json -X GET | grep -e “bytes” -e “name”
if [ $? -ne 0 ]; then
echo “Error $? listing files”
exit 1
fi
exit 0
;;
*) echo “Error: argument not recognized.”
echo “Usage: $0 [-l / -d / -u] [FILE]”
exit
;;
esac
Per aprire una finestra su Ubuntu
(CTRL+ALT+T)
Per digitare la parentesi graffa tramite pc con tutti i tipi di tastiera:
Per le parentesi graffe in tutti i Sistemi Operativi, basta dare:
Shift + [ (che si traduce poi in Shift + Alt Gr + è) per la parentesi aperta {
Shift + ] (che si traduce poi in Shift + Alt Gr + +) per la parentesi chiusa }
Cliccate sulla tastiera contemporaneamente i tasti “Alt” e “123” per generare la parentesi aperta (“{“) e “Alt” e “125” per la parentesi chiusa (“}”). Per i numeri è necessario utilizzare la tastiera numerica posta sulla destra della tastiera;
Nei sistemi Unix la tilde (cioè questo caratterino ondulato: ~) è un carattere molto utile perchè se scritto in un path rappresenta la cartella home dell’utente
Infatti per la tilde lo schortcut è:
Alt Gr + ì
Hubic è un servizio di cloud con 10 tera per solo 5 euro al mese.
Ho avuto la necessità di montare il mio account su linux con hubicmount
Prima di tutto installo le dipendenze
apt-get install build-essential libcurl4-openssl-dev libxml2-dev libssl-dev libfuse-dev libjson0-dev pkg-config libmagic-dev
$ ./configure make sudo make install
sudo hubicfuse /mnt/hubic -o noauto_cache,sync_read,allow_other
/etc/fstab:
hubicfuse /mnt/hubic fuse user,noauto 0 0
$ sudo addgroup fuse
$ sudo usermod -a -G fuse [username]
Quando affrontiamo un problema o abbiamo un’idea, spesso intuiamo la soluzione ma non siamo in grado di formularla in modo operativo per metterla in pratica. Il pensiero computazionale è proprio questo, la capacità di immaginare e descrivere un procedimento costruttivo che porti alla soluzione. Come imparare a parlare ci aiuta a formulare pensieri complessi, così il pensiero computazionale ci offre strumenti ulteriori a supporto della fantasia e della creatività.
Con il pensiero computazionale si definiscono procedure che vengono poi attuate da un esecutore, che opera nell’ambito di un contesto prefissato, per raggiungere degli obiettivi assegnati.
Per questo il pensiero computazionale è per tutti!
E’ una capacità trasversale che va sviluppata il prima possibile. Non è solo per informatici e programmatori, ma programmare è il modo migliore per acquisirlo. Per questo in Europa e nel mondo si svolgono ogni anno campagne di alfabetizzazione per la diffusione del coding. E’ per questa stessa ragione che noi parleremo di coding e giocheremo con la programmazione senza ripeterci ogni volta che lo facciamo per sviluppare il pensiero computazionale. Quello accadrà da sé senza bisogno di dirlo.
Il pensiero computazionale è un processo mentale per la risoluzione di problemi costituito dalla combinazione di metodi caratteristici e di strumenti intellettuali, entrambi di valore generale.
I metodi caratteristici includono:
Questi metodi sono importanti per tutti, non solo perché sono direttamente applicati nei calcolatori (computer), nelle reti di comunicazione, nei sistemi e nelle applicazioni software ma perché sono strumenti concettuali per affrontare molti tipi di problemi in diverse discipline.
Gli strumenti intellettuali includono:
Anche per questi strumenti i benefici si estendono al di là della disciplina informatica.
espectacular! una pregunta, es pot llegir el gid del telefòn que estàs escoltant amb el dongle?
gràcies!
Hola! Primer de tot vull especificar que no he pogut acabar d’aconseguir-ho però sé que és possible! Referent a la teva pregunta.. pots especificar més que és el gid del telèfon? jeje Gràcies per interessar-te i a la teva disposició!
Doncs en refereixo al Global ID o identificador únic del terminal, l’intenció no es crackejar o intervenir el telefon si no saber quin terminal tinc aprop.
Merçi!!
El que pots arribar a veure és el TMSI que és el identificador del terminal respecte la torre!!! Per saber la situació o quin tens a prop hauries de saber el Cell ID que és el identificador de la torre BTS de GSM i aquest nombre si que el pots saber amb el dongle !!!
Espero que això t’hagi contestat la teva pregunta😉
Hi, In step 8 you talk about decoding SMS and voice call. But airprobe can decode only the downlink traffic. So what kind of SMS do you decode? And what kind of voice call do you decode?
It’s like you’re only able to decode the phone calls and SMS messages of people that sends or calls at a nearby tower from where you are.
ferran que podrias ayudarme un con el tema de kraken,para acabar de pulir esto?tengo unas cuantas dudas.Espero que puedas hecharme una mano y no te moleste.Te dejo mi correo electronico escribeme! nestor_1990_20@hotmail.com
Un saludo
Quizás tengo un rato alguna hora y en ese caso te puedo ayudar! Envíame un correo con tus dudas bien detalladas y veré qué puedo hacer! PD: Mi correo está en la pestaña “about”!!!
Hello. I’m trying to understand how can i intercept Sim Toolkit comuunication from carrier. do you have any ideas how can i see information which carrier sends to SIM, i’m unsing android
I’m sorry, but I have no idea to do this! It’s been a long overdue since I did all this stuff. But in this other topic I can not help you at all!
I would like to help you but I don’t wanna enter to things that I only have a basic idea.
Hope you like my topic! Kind regards.
Ferran.
Hi mate
this really interesting my aim to establish my SAT network via VOip but I have no idea could you pls help me to decode my out calls hence I am using airtime I dont wish my company to see outband calls
Hey! I think I can not help you with that!
Hope you enjoy my blog!
Ferran.
Hi,
Which antenna did you use with rtl-sdr ? was it the one shipped with the stick or some other ? which antenna to use for best reception of GSM?
I was using the one in the photograph, that is a normal omnidirectional antenna for TV reception! But I was in a quite good zone without many buildings surrounding the place. So for a better reception I recommend you using a real ADS-B antenna like that: http://www.google.de/imgres?imgurl=http%3A%2F%2Fwww.amateur-radio-antenna.com%2Fimages%2Fumtsgprsrsantenne1.jpg&imgrefurl=http%3A%2F%2Fwww.amateur-radio-antenna.com%2Fgsm-antenna-mobile-phone%2Ftriband%2Fumts-3g-gsm-antenna-umts-gsm-rs09-21.php&h=595&w=612&tbnid=iMRqVp4vyKi1FM%3A&zoom=1&docid=Tuz_rBcFvDMbdM&ei=L0H8U6jKOqnU4QSp5oHwDA&tbm=isch&iact=rc&uact=3&dur=281&page=1&start=0&ndsp=42&ved=0CEAQrQMwCg
This will improve your reception! But as you should know you have to position the antenna in the top of your building house or whatever!
Regards,
Ferran.
Could please provide me your email or a number.
here is my email bader@engineer.com
Thanks for getting back to me Ferran
https://ferrancasanovas.wordpress.com/about/ here is my email address!!!
The rtl2823.cfile mentioned above does not open in the gnuradio 3.7. So for people using the latest version of gnuradio just replace all gr_ to blocks_ in the file to make it work.
Carissimo, vorrei acquistare il software